In today’s digital world, cyber threats are constantly evolving. To protect networks from unauthorized access...
Showing all 2 results
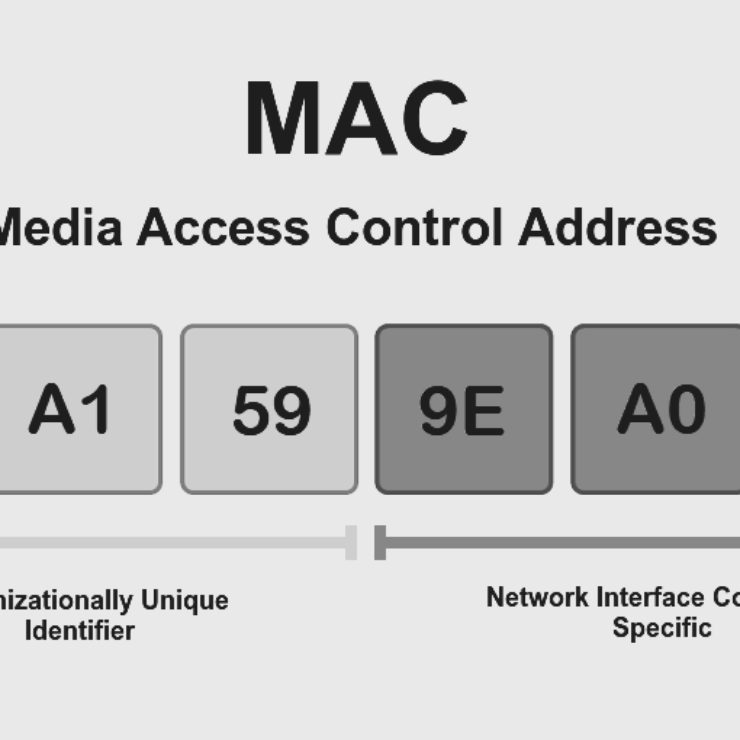
Introduction In the realm of networking, devices must have unique identifiers to communicate efficiently within...